Chapter 4 – Using email safely
Electronic mail (e-mail) is the computer equivalent of traditional mail. It has the advantage of speed and negligible cost. However, it is often misused to reach large numbers of users in order to spread misinformation or unsolicited commercial messages. Another goal is to obtain confidential information and then misuse it.
1. Introduction
Electronic mail (e-mail) is the computer equivalent of traditional postal mail. Text from a postcard, correspondence card or letter can also be written and sent via e-mail. Files can also be attached to e-mail messages – documents such as contracts, invoices, photographs, etc., which in the real world would be the equivalent of sending a parcel.
E-mail offers a huge advantage in terms of speed and cost of delivery. In earlier times, a messenger would carry a parchment with a message for weeks, and with the advent of motorization, the delivery time was reduced to days. Sending electronic mail takes seconds and costs virtually nothing. For these reasons, it is often abused to address many users, for example, to elicit confidential information using manipulative social engineering methods. It is also used to spread misinformation and unsolicited commercial messages. Once you gain knowledge about these practices, it will be easier to resist them.
2. How e-mail works
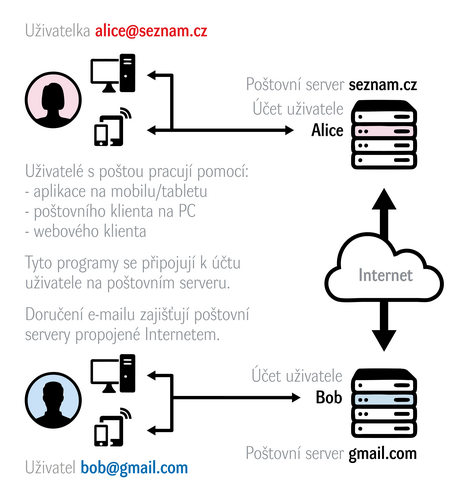
Anyone who wants to use e-mail, i.e. send and receive messages, must have their user account set up on an e-mail server, i.e. an e-mail box. This is usually set up for the users by their employer or the educational institution they attend. However, it is now common for almost everyone to have a private email account with a free email provider, e.g. gmail.com, seznam.cz, etc. Each mailbox is assigned a unique e-mail address, e.g. alice@seznam.cz
The users then use their mailbox – i.e. view their inbox, write and send messages – using specialized applications, so-called e-mail clients. These applications usually offer additional features that make working with e-mail easier, such as being able to work with electronic signatures and message encryption, sort incoming mail into folders, recognize spam or proactively alert you to suspicious inbox content.
An e-mail client can be a classic application that must first be installed on a computer, tablet or smartphone. This type is also called a native application. E-mail providers usually also run a web interface called webmail, which provides the same functionality as the installed application. The advantage is that the users can access their e-mail from any device with a web browser.
Not all the e-mails are the same
In general, the word e-mail is used to mean both electronic mail and an e-mail address (“What is your e-mail?”), but also a message sent by electronic mail (“I will send you an e-mail.”) It is such a universal word in electronic communication that its meaning should always be inferred from the context.
3. How to use e-mail correctly
Electronic mail is now considered a standard method of communication in both business and private life. However, it should be used cautiously because improper use can lead to information leaks, the spread of alarm messages and other problems.
Password for e-mail box
The e-mail box is often the most important of all services used on the Internet because registrations for other services are frequently linked to the user’s e-mail box. Recovering a forgotten password for the above services is usually possible by sending a message. If the e-mail box password is lost or stolen and misused, it is possible to lose a lot of confidential information and messages stored in the account and access to many other services linked to the e-mail address.
For this reason, your email password should be unique, i.e. not used elsewhere, sufficiently complex and changed regularly (see the chapter Who I am and what I am allowed to do).
Message sender
An e-mail message, just like an ordinary letter, is written entirely by the sender and, like an ordinary letter, the sender can write any information on the envelope, including a non-existent or stolen address of another sender. The message then arrives, and although everything indicates that it came from a known specific person, it could have been sent by a fraudster who is only impersonating that person. Therefore, you cannot blindly trust the From: field; an e-mail is only trustworthy if it contains an electronic signature (see Encryption and Electronic Signature). If you are not sure whether the person has actually sent the message, verify it by other means than another e-mail message, such as a phone call.
Sometimes, someone can also misuse your e-mail address and include it as a sender in the e-mails you send. Such messages will then appear to have been sent by you. And if someone sends a message to a non-existent address, you may receive a message about the inability to deliver a message that you did not personally send. In such a case, there is no need to panic as it does not necessarily mean that your password has been misused. The e-mail message contains information about where or by whom it was sent, so if you find yourself in such a situation, forward the e-mail to your user IT support, where experts will assess the specific message and give you recommendations on how to proceed.
E-mail and digital footprint
As already mentioned, electronic mail is similar to conventional mail. Still, it is impossible to trace the shipment route when sending a regular letter without a delivery note and, therefore, without a shipment number. This is not possible in the case of an e-mail message because each message leaves behind several traces. In a regular e-mail message, these traces are not visible but are hidden in the e-mail header, which e-mail clients can view. The header records information from all mail servers the message has passed through, so it is possible to determine from which computer the message was sent and when, which can tell us a lot about the sender. Other records are stored and archived in the operational records of mail servers.
E-mail attachments
In addition to text, electronic messages can contain any files (called attachments). These can be documents, photos, but also some executable and therefore potentially harmful files. In most cases, an executable file, which is typical of viruses (generally malware), cannot be sent as an email attachment because the sender’s email server will refuse to accept it as unsafe. So attackers usually use macros in Office package files or scripts in PDF files, which typically pass through the e-mail server successfully. Sometimes, the malicious files are not directly part of the message, but the message may contain a link to download them.
Do you know what the following terms mean?
Executable file – is a file that contains a set of commands that the computer understands and executes. In the Windows operating system, it has the extension exe (i.e. executable).
Macro – is often part of office package files (Word, Excel) and allows you to execute a set of commands just like an executable file.
Script – a script is a file containing a set of commands for a scripting language, of which there are many.
If you receive an electronic message with a suspicious attachment, the best defence is not to open the suspicious files or to contact user support. At the very least, if you do open them, do not enable macros, allow PDF files to run scripts, or connect to the web (these activities require active user confirmation). Often antivirus software on the mail server or workstation can also help prevent delivery or opening of detected malicious files.
If you want to send an electronic message with an attachment, it is important to remember that email is not primarily designed for sending large files, so you should not send them. One reason for this is that email inboxes are usually limited in size, and you might overwhelm the recipient’s inbox, or the destination server might not even accept such an email.
E-mail attachment size
There is no generally defined maximum email attachment size. Some mail servers limit it to 10 MB, but this is highly individual. The capacity of mailboxes also varies, so it is difficult to determine a reasonable email attachment size. In practice, however, it turns out that the globally acceptable size for the email world is in the order of megabytes (MB).
Mass mailing
Mass mailing is used when you want to reach a large number of recipients on the same subject. The best way to avoid these situations is to use mailing lists. A mailing list is an automatically, manually or voluntarily created group of people (or their email addresses), who have a common interest or function/position in the organisation, e.g. secretaries/students. This group has its own email address to which a message is sent and this message is then delivered to all the people in the group. If it is necessary to use mass mailing, follow the rules that minimize the risks associated with this method of communication. First, it concerns the misuse of e-mail addresses and their links (who is communicating with whom) to send spam and fraudulent messages. If a recipient’s mailbox is compromised, an attacker will find out the email addresses of other people who may know each other or have common interests, and can use this information to send spam, misuse the address, or launch a more sophisticated cyber attack against those people.
When writing a bulk message, you need to ensure that individual recipients do not see the addresses of all the other recipients. This can be done by simply adding the email addresses of all recipients to the Hidden copy:, Bcc:,.
Chain e-mails
You have probably received a message like this: “Send this message to 10 other people, or you will get sick within a year and a day.” Such bulk messages travel through email inboxes and from time to time they return to the sender, the cybercriminal, who then collects working email addresses where someone is reading and actively using the email, also taking advantage of the link of who is sending messages to whom. Cybercriminals can then send unsolicited messages with personalised content, which generally have a higher success rate.
Netiquette
Did you know that there is a list of ethical behaviours on the Internet called netiquette? You can find lots of interesting information there to help you behave online in a way that other decent internet users expect. Read more about netiquette at http://www.netiketa.cz/.
Spam
Every e-mail address eventually becomes public knowledge, whether by being listed in a publicly available directory on the institution’s website as a staff contact, by being included in mass mailings, by registering for competitions and e-shops, or simply by use.
Since anyone can send a message to a known e-mail address, it is impossible to ensure that e-mail messages from various advertising agencies, political groups, etc., who are happy to reach the masses easily, do not end up in e-mail inboxes. In the real world, spam can be compared to a leaflet campaign. However, sending an e-mail costs almost nothing, so that you can send many of them to everyone. These emails that we don’t care about, called spam, statistically account for up to 98% of all inboxes. The fact that we do not see it is due to spam filters on mail servers and in mail clients, but they cannot be 100% successful, so we need to be aware that occasionally some spam will arrive, and we must be able to ignore it.
Battle between spam and anti-spam
Spammers are well aware of the capabilities of e-mail server administrators and can torment them considerably by bypassing spam filters. It is then very difficult for the administrator to find a way to automatically detect spam correctly. The problem arises if the rules are too strict. Then, even an utterly regular e-mail ends up as spam, which is highly undesirable.
Never send spam – it is unethical, and if it is an unsolicited commercial message, you are also in violation of the law. However, someone else can also send spam from your mailbox if they obtain your access details. So be careful with your e-mail mailbox password, and be especially wary of phishing (see below). The operator of the abused mailbox usually blocks it very quickly and does not care whether the spam was sent by the user or by someone else on their behalf.
Phishing and social engineering
Phishing is a fraudulent technique used on the Internet to obtain confidential information from users. It is typically aimed at stealing and misusing login details or credit card numbers. Typically, a phishing message is sent by email or other means to create a sense of urgency in the victim, or a non-existent problem that needs to be addressed urgently. The sender often pretends to be an authority figure, such as a boss, system administrator or office worker. These methods in the message are intended to distract attention, scare and leave little room for thought. They are known professionally as social engineering techniques.
The received electronic message will either contain a simple text form that the attacker asks you to fill in and send back, or, more often, a link to a fake site with a login form that, once filled in, will send confidential information, i.e. a login and password to the attacker. In addition to the form and the link to the fake page, it can also contain a dangerous attachment with malicious code. The attacker forces the victim to open the attachment and run the malicious code on their computer, which allows them to gain control over the computer. For example, they can obtain a log of keystrokes, which will enable them to get login details. When you receive an electronic message, you should always check who is actually sending the message, and if they are asking for confidential information, you should be cautious and suspicious. For example, before sending such information, you should verify by phone that the person named in the electronic message has actually sent the message.
Warning
A bank or administrator of any service (e-mail box, social networks, etc.) never needs a user’s password to manage a user account. If you are asked for your password, it is a scam. Never reveal your password!
Hoax
A hoax is a false, usually alarming message spread by mass mailing or by forwarding. Often, hoaxes have the character of a chain message, i.e. they contain a request to send them to other people. Such messages should be verified by common sense or at https://hoax.cz and should definitely not be forwarded. Alternatively, it is also advisable to warn the sender that he/she is sending a hoax so that he/she will think twice before spreading untruths and ruining his/her reputation.
4. Summary
After reading this chapter, we know that using e-mails is easy. To send an electronic message, all we need to do is have our email account set up and know the e-mail address of the person we want to send the message to. The mail servers will then take care of the delivery of the message. Based on how electronic mail works, sending messages leaves a clear digital trail, and it is, therefore, easy to track where the message has travelled.
Even when working with e-mail, certain principles must be followed to avoid problems with misuse of the e-mail service. This includes behaving in a way that does not play into the hands of potential cybercriminals – for example, choosing a strong login password, sending bulk messages correctly, etc.
We have explained why it is advisable to avoid mass mailing and what rules we must follow, that spam is comparable to a leaflet campaign, and that if I am not interested, it is better to delete the messages. We already know that phishing messages try to trick people into revealing confidential information, such as passwords, and that a hoax is a false, alarming message. We also know that email messages can carry attachments, which can be any file, including viruses and other malicious code.